Stop Advanced Attacks with EDR
Defend against the latest threats with intelligent endpoint detection and response, purpose-built for Mac. Get maximum security with minimal agent overhead.
Book a Demo- No credit card required
- Free access to all features for 14 days
- Free access to support
Setting the standard in Mac security
Kandji’s security research is the cutting edge of threat detection and prevention. 2024 highlights include:

Security researchers were the first to discover and report vulnerabilities affecting Sequoia, Sonoma, and Ventura.
First to discover and protect against numerous threats and malware variants targeting Mac computers.

Security researchers presented on their discoveries at cybersecurity conferences around the world.
Stop more threats
Leading protection against malware and emerging threats is driven by threat intelligence, machine learning, and a dedicated security research team for Mac.
Lower the cost of ownership
A single agent for EDR and MDM enables instant deployment, while automated threat response gives time back to IT teams.
Keep users productive
Built natively in Swift, the Kandji Agent uses Apple's Endpoint Security framework to consume minimal resources and deliver real-time protection.
Backed by dedicated security research.
Accelerated by AI.
Security researchers
Kandji security researchers analyze emerging threats, attacker trends, and endpoint event insights to build proprietary detection models that stop new attacks.
Machine learning
Machine learning models millions of detections and events. These models identify patterns of malicious or anomalous behavior and power detections to stay ahead of attackers.
Key functionality
Instant endpoint protection with automated response and effortless interactions.
File detections
AI-enhanced file analysis stops malware and unwanted programs. Backed by Kandji’s Security Research team and global threat feeds.
Behavioral detections
Real-time process monitoring detects sophisticated threats instantly, stopping advanced attacks before they spread.
Protect Mode
In Protect Mode, the Kandji Agent blocks or kills any malicious processes and quarantines files. Deep integrations with Apple’s Endpoint Security framework allow for real-time response.
Detect Mode
In Detect Mode, the Kandji Agent detects the event, creates a threat event, and generates an alert. It does not take action to quarantine files or block processes.
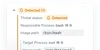
Set removable storage controls
Lock down external storage access on Mac with encryption and access permission controls for USB drives, DMGs, SD cards, and server volumes.
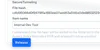
Release files from quarantine
Admins can release specific files from quarantine across all devices and add them to the allow list in one easy workflow.
Investigate threat events
See exactly what files or actions triggered the event, along with all critical details needed to investigate the threat and assess its impact.
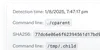
Enforce allow / block lists
Allow or block files by hash or path. The Kandji Agent ignores allowed items and treats blocked items as malware.
The fastest to deploy. The easiest to work in.
Unified platform deploys MDM and EDR via the Kandji Agent, eliminating deployment time and ongoing maintenance.
Kandji Security Research
- Threat IntelligenceMay 23, 2025
Dissecting the macOS 'AppleProcessHub' Stealer: Technical Analysis of a Multi-Stage Attack
On May 15, 2025, the security research team MalwareHunterTeam (@malwrhunterteam) identified a suspicious file named libsystd.dylib with low detection—
Keep reading - Threat IntelligenceMay 9, 2025

Kandji Quarterly Threat Intelligence Report: May 2025
Welcome to the Kandji Threat Intelligence Report, our quarterly summary of emerging threats in the macOS ecosystem and how Kandji is responding in rea
Keep reading - Threat IntelligenceMay 1, 2025
macOS Vulnerabilities: A Year of Security Research at Kandji
Kandji security researchers have been hard at work hunting for vulnerabilities in macOS, reporting them to Apple before malicious actors can exploit t
Keep reading

Manage and secure your Apple devices at scale.