2024: Kandji's Year in Review
In 2024, Kandji continued to revolutionize Apple device management with groundbreaking innovations, powerful new integrations, and significant improvements to our core platform.
Keep reading
Table of Contents
Mobile device management (MDM) is the practice of remotely administering mobile devices—from smartphones to laptops—using software that provides a single point of control. With MDM software, IT departments can manage an organization’s entire device inventory to protect corporate data, standardize configurations, and ensure user access to authorized software and services, all without disrupting the end-user experience.
Born of the bring-your-own-device (BYOD) trend, when employees began using personal mobile phones for work, mobile device management software has become a critical part of maintaining endpoint security and regulatory compliance. The vast majority of exploits target endpoints, mobile or otherwise via unpatched software, phishing, or insecure Wi-Fi connections. Mobile devices carry with them the risk of users downloading malicious mobile apps or of devices falling into the wrong hands. And when those mobile devices have access to corporate resources, those corporate resources can fall into the wrong hands.
Mobile device management solutions address such challenges by (at a minimum) maintaining a device inventory, enforcing password protection, and offering the ability to lock or wipe lost managed devices remotely. But today’s modern MDM tools go much further to monitor device activity, control which apps can be installed, mandate encryption, promote data security, and more. Mobile device management also extends to establishing standardized device configurations and software environments as well as user-driven setup routines.
Exerting organizational control while empowering users, while also meeting compliance standards demanded by partners and governing authorities, is the strategic goal of MDM. Lawyers, IT managers, and security professionals may establish those policies, but MDM software enables IT departments to enforce them at scale.
Apple MDM software uses a classic client-server architecture, with a twist. The server holds all the parameters, configurations, and settings for devices along with policies and user profiles.
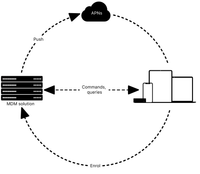
Most MDM servers reside in the cloud and are maintained by the MDM provider, although some providers also offer locally installable server software. Admins use a server console to adjust device configurations, update software, and implement security policies in real-time. Mobile device operating systems include APIs to give agents the required control.
Some MDM platforms work across Android, Apple, and Microsoft devices, while others are platform-specific. Devices have varying capabilities, so cross-platform MDM solutions focus on features common to all devices, while platform-specific MDM solutions can exploit the full range of features a given operating system offers. Many companies square that circle by running cross-platform and platform-specific MDM software side by side.
The ideal is to craft policies carefully and, once the various setup and configuration hurdles are cleared, shift the burden of maintenance to MDM automation. At the same time, admins must have the ability to accommodate users and devices with unique needs via customized settings.
Over time, organizations have demanded more from MDM. What began as a way of tracking and securing smartphones remotely has extended to a slew of additional features and devices. At a minimum, today, MDM solutions can enforce security settings on different types of devices, offer data encryption capabilities, and allow admins to apply role-based controls to individual users. Extended capabilities beyond those have given rise to several other families of services:
With MDM as the foundation, EMM supports synchronization with an organization’s directory services (such as Microsoft Active Directory) and/or identity and access management solutions (such as Okta or Ping Identity). EMM also adds MAM (mobile application management), which enables admins to distribute and update software for a fleet of devices simultaneously and establish policies for specific applications across various device types. MCM (mobile content management), which controls which applications can access or transfer an organization’s data, also falls under the EMM umbrella.
UEM goes further than EMM to include every endpoint computing device in an organization, including desktop systems. All the capabilities of an EMM solution apply, plus the ability to provision and monitor a company’s entire catalog of nodes. UEM solutions typically include a dashboard to verify the status of every device, whether that device is offline, online, correctly configured—or online and improperly protected. UEM is an appealing concept, but difficult to pull off: The diversity of platforms and their continuous operating system updates makes it difficult to provide deep device management functionality across the board.
The fact is that none of these other acronyms have achieved anywhere near the currency of MDM. Outside of the tech industry, most business customers refer to the whole catalog of device management capabilities as MDM, including those associated with EMM and UEM.
Careful planning can ensure an MDM initiative succeeds. Even small organizations that believe they need minimal MDM capability to track and secure devices need to consider what other functionality may be needed down the line—and develop an extensible MDM strategy to match.
Know your endpoint and application environment: As with other aspects of IT, the difficulty of discovering what’s currently in place can’t be underestimated. Employees typically use multiple devices for work, and each one will need to be provisioned with an MDM agent compatible with the operating system in use. Which mobile apps are being used for work and which enterprise applications are being accessed by users also need to be determined to develop a full application security profile.
Determine your security and compliance goals: Virtually all MDM solutions integrate with endpoint security software, but the ease of that integration varies widely. Alternatively, some MDM solutions come with a full suite of endpoint security capabilities, so MDM and cybersecurity can be managed from the same point of control. Meeting such information security standards as ISO/IEC 27001 is obligatory for some industries, so organizations need to choose MDM software that has all the functionality necessary to get there.
Try out MDM solutions before committing: A checklist of desired features and compatibilities only gets you so far. MDM software varies widely in its usability, particularly when it comes to grouping users and devices and making wholesale changes from the console with a single pass. Fortunately, most MDM solutions are cloud-based (as opposed to on-premises), so it’s easy to sign up for a trial account and give one a spin.
Take advantage of MDM automation: The whole point of MDM is to avoid manual configuration of devices. For example, the ability of an MDM solution to download and distribute software updates to operating systems and applications with minimal admin intervention can save a great deal of time and effort. The less admins need to touch an MDM solution, the better.
Carefully configure monitoring and alerts: MDM dashboards should clearly show the status of an entire fleet of devices. The loss or compromise of an endpoint should fire off an alert, but parameters should be adjusted so false alarms rarely occur. Complete, easy-to-read reports can provide the forensics to optimize MDM deployments and identify potential trouble spots.
A good way of looking at MDM is as a vehicle for implementing and enforcing policies. Those policies need to be developed with the aid of security professionals, resulting in a template for device configurations and controls—as well as a basic evaluation instrument for choosing an MDM solution. Note, however, that policy changes will inevitably occur and implementing such changes across a fleet of devices should be as straightforward as possible.
Several popular MDM solutions can manage Android, iOS, MacOS, and Windows devices, while others focus on a subset. To manage Apple devices, MDM software simply needs to support the Apple MDM protocol—which nearly all players in the space do. But iOS and MacOS devices possess a number of unique features that only an Apple-specific MDM solution such as Kandji can exploit.
First among these is the ability to work hand in glove with Apple Business Manager, used by virtually all organizations that deploy Apple devices. Apple Business Manager is a web portal that admins can use to purchase Apple hardware and software and track Apple device inventory. It’s meant to be coupled with an Apple MDM server, a combination that among other benefits enables zero-touch deployment, where admins pre-configure new devices over the network with complete, user-driven setup routines.
Apple Business Manager and an Apple-specific MDM solution together have other advantages. For one, all devices known to Apple Business Manager are automatically enrolled in the MDM system. Plus, when integrated with an organization’s directory service, Apple Business Manager automatically generates a Managed Apple ID for each Apple user, the first step in creating user profiles that associate users with devices and delineate various rights and permissions.
Another benefit of an Apple-specific MDM solution is automated remediation: When an unauthorized change is made to an Apple device, it’s corrected automatically, without admin intervention. Capabilities vary among Apple MDM solutions, but admins may also enjoy automated patching for iOS and MacOS along with automatic updates to all organization-approved apps.
MDM software has established itself as an indispensable tool for IT. What began as an answer to the security vulnerabilities of personal mobile devices has expanded into a powerful control center for not only tracking and securing an organization’s fleet of devices, but for managing multiple software environments tailored to specific device types and their users.
Admins routinely note the amount of time saved by using an MDM system, particularly when well-crafted automation relieves them of having to implement updates manually. The degree of benefit, of course, depends on the capabilities and ease of use offered by a specific solution—particularly when it comes to managing changes among groups of users and devices. But the bottom line is that no organization larger than a mom-and-pop business can afford to go without an MDM solution.
Speaking of which: How much to Apple MDM solutions cost? They vary widely in price as well as capabilities. They are typically priced per device or for a range of device counts.

In 2024, Kandji continued to revolutionize Apple device management with groundbreaking innovations, powerful new integrations, and significant improvements to our core platform.
Keep reading
Discover the trends shaping enterprise technology as Apple devices continue to gain ground in the corporate world.
Learn more
Watch the virtual event recap from our latest product announcement. Kandji unveils new assignment features and automations that make administration easy and efficient regardless of scale and complexity.
Watch the event